Augmentable, Believable, Improvable and Invisible.
Teaser - A Design Fiction
Peter always saw Lisa on the metro train home. He wanted to approach her but, instead of coming up and say hi, he tried to find her online. Putting together the observed characteristics of Lisa and pretending to be the guy Robert who said hi to her once on the train, Peter had Lisa accept him as a friend in the virtual network.
Carefully he created a desirable picture of himself through a falsified identity seen by Lisa alone, based on the algorithmic analysis of her online profile, activity history, group discussions and contact list. A chatting history among her network friends has shown Peter an opportunity to meet Lisa in real life, making her reach out naturally to him.
With everything planned out and the handy tips of talking ready, Peter went to the bookstore where Lisa works part-timely as a store assistant. Everything happened as expected, except, however, the fact that Lisa was not there to talk to him, and neither does she work at the store...
About
Augmentable, Believable, Improvable and Invisible Investigates how social media users craft virtual identities, manage reputations and augment real-world relationships based on misleadingly sharing of personal information. The project envisions a series of services that incorporate deception (e.g lying, hiding, concealing and disguising) as a fundamental affordance of the design for social networking experiences.
The augmentable me, the believable me, the improvable me and the invisible me are the personas resulted from four main topographies of manipulating public and private data strategically. The summary of these personas led to a design proposal that translates the observational and quantitative research into a series of user experiences and scenarios.
1 / 2 / 3 / 4 / 5 / 6 / 7 / 8 / 9 / 10 / 11 / 12 / 13 / 14 /
The Augmentable Me
1 / 2 / 3 / 4 / 5 / 6 / 7 / 8 /
Who is the 'Augmentable Me'?
Augmented identities are the result of actively crafting, reflecting and commenting on who we are, as opposed to truthfully sharing all the personal information. The 'Augmentable Me' is driven by the motivation of a better self-image in front of the chosen audience, and based on what one wants to gain out of being the way they choose.
"It is human nature to hide their backstage language from being seen by a social group. The backstage language consists of reciprocal first-naming, profanity, open sexual remarks, rough informal dress, 'sloppy' sitting and standing posture, mumbling and shouting, playful aggression and 'kidding', humming whistling, chewing, nibbling, belching and flatulence." - Erving Goffman
The Discovery of the 'Augmentable Me'
50% of the social network users aged 13 to 21 claim that they have falsified information in their online profile. Over 10% of the MySpace users are over 100 years old. Are they really that old or they lied about their ages? A linguistic study of men and women during a dating event found these people on average lied 20 times in an hour long conversation, which is once every 3 minutes.
Lying does not directly refer to the misleading online behaviors, but rather a condition of being human in regular social courses. But more interesting questions arouse when we find that though 'lying about age' is common among both MySpace and OKcupid users, OKcupid users lie more conservatively. Why? People augment their informations based on the odds of real-world encounters and how these information being acquired by their designated audience. The fact that personal information is insuitive and pervasive online, calls for more awareness of the computational behavior of a particular social plaotform, in order to understand what is seen by who, where, and under what circumstances.
Social networks create expectations for who we are
This is an research experiment aimed to discover how different social sites regulate user behaviors of 'creating public profile.'
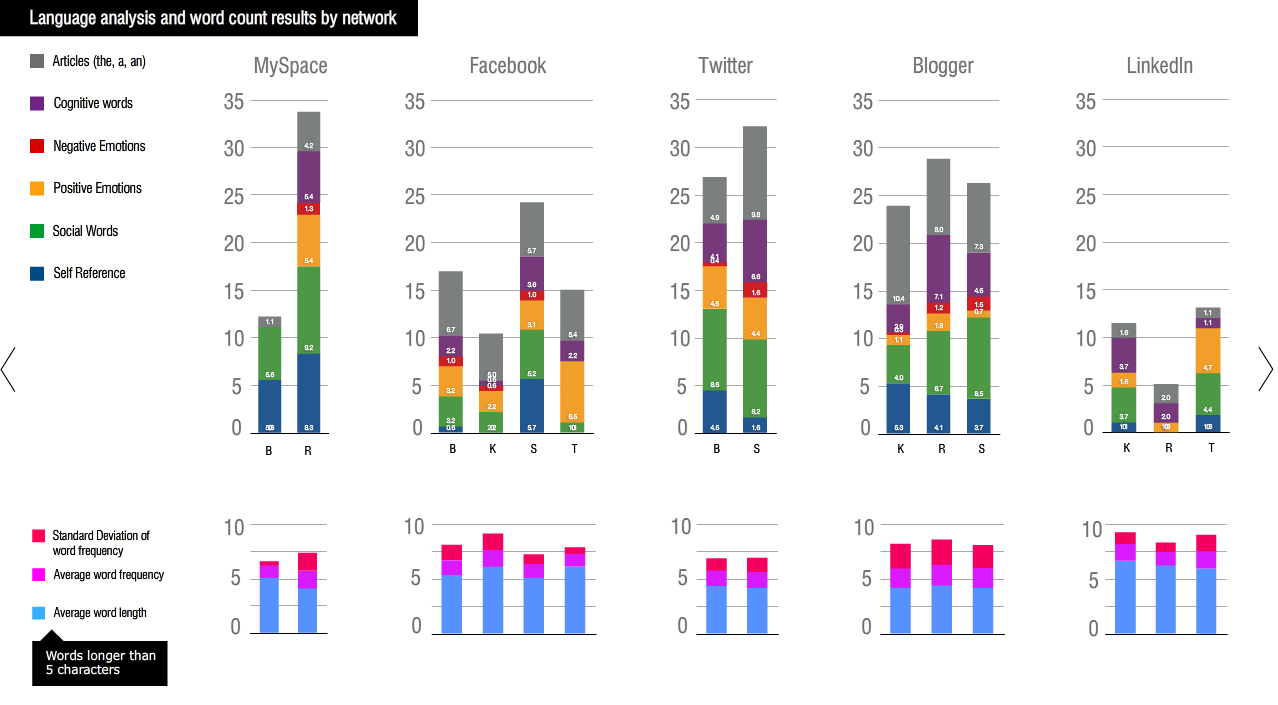
I collected 5 people’s profiles from 3 different social networks, removing their names, and asked 5 others to draw a portrait of each profile. The text-based profile is also parsed through the word count algorithm LIWC that gives a rough personality report. It was my intention to juxtapose the drawings and the language analysis results to spot points of mismatches and to investigate the reason for the mismatch. Here are the major findings:
(1)Overall, the disposition of the portaits match the personality analysis result. (2)When the data is not enough to make a judgment, the illustrators were confused just as the computer does. (3)Stereotype is the tool for people to perceive others, which is more apparent or dramatic than the automated analysis. (4)Social network creates expectations of users, the difference between one user's profile on different social networks turns out to be even bigger than that between different users in one social network.

Self-curating Vs. actual happening
This experiment visualizes the gap between the actual and self-curated happenings(via social media) in a daily course.
I gave my friend a GPS data logger and tracked her for two weeks, while keeping myself updated with her Facebook status, Twitter feeds and Foursquare check-ins. I wrote down what I think her schedule is based on the information she shared online. The GPS data were played back in a timeline with the posts overlapping it. Then I came to realize the laps between her move and her online updates, and there are gaps between what she did and what she said she did. The 'live feed' seemed it never happened.
The Believable Me

Who is the 'Believable Me'?
The 'Believable Me' is also known as the 'Plausible Me', a term originally coined by Laurent Haug. The 'Believable Me' is a virtual identity associated with credible, authentic informations of a real person, regardless of whether what has been said or done is real.
The 'Believable Me' is motivated by the intention of preserving privacy through selectively spreading one's private information to the world. Our increasingly open presence online has resulted in a debate whether our privacy is lost forever. I would like to take a skeptical standpoint that while our identity becomes more open it is also open for interpretation.
Haug indicated the affordance of social media for fabricating happenings, and one creates a credible space where people "expect to see information about you". "Whatever credible information you say in there will be taken true by the world." However the stake of such credibility lies in the overlapping moments of virtual- and real-world encounters. It is not difficult to fabricate a convincing story once. But how to keep it consistent over time? And what if the 'Believable Me' has become so convincing that we need to adjust the real-world behaviors accordingly to maintain our identities?
"If you want to introduce yourself, do not begin by saying "My name is Aaron and I like traveling." show evidence like photos, diaries, souvenirs, etc. If necessary, photoshop yourself in front of the landmark."
The Discovery of the 'Believable Me'
The notion of privacy has changed in the digital living, when the boundary between the virtual and the real has dissapeared. Restricting personal information holds one back from using the services and disconnect them from important social contacts. Instead, giving away permissions to designated groups or individuals help one redeems the ownership of their digital presence.
"Privacy is costly. Withholding unflattering personal information may constitute a form of deception. To the extent that people conceal personal information in order to mislead, the economic case for according legal protection to such information is no better than that for permitting fraud in the sale of goods."
– Richard Posner
Should privacy be considered as 'permission' instead of 'restriction'?
This project maps out the history of privacy, by distinguishing historical adaptations people made towards different technologies. The evolution of the notion 'Privacy' has indicated that future social services will focus on facilitating more open but playful management of identities. The services will also withdraw support from cognitive technologies that interprets user intentions behind the information sharing and using the accumulated behavioral data to predict and guide future decisions in social courses.
What does sharing mean in the new sense of online privacy?
Sharing is the new gesture of claiming ownership to our identity. This project is a result of thinking about the physical metaphor of 'updating' virtual status. The two-sided book has a display facing outside, with the content changing based on what the owner is reading.
However, what the book invites one to do, is creating misleading descriptions to their identity, and hiding away from public attentions. One may be reading a cheap novel while the book broadcasted scholarly topics on socio-economics.

Risk Vs. Service
In a conversation with Saikat Guha, an online privacy expert and encryption engineer, we discussed what may be the trending changes and challenges for designing next generation online privacy tools. It is a common insight that most users surrend their privacy to the temptation or necessity of using the service, until they find their privacy is violated. This is known as the 'dilemma between risk and service' among the encryption experts. Saikat's earlier researches have dealt largely with social website's privacy service from the benefit for both the user and the advertiser: how to maximize the user experience with least risk of privacy, and to help advertisers reach the targeted market more efficiently. Saikat’s latest research has shifted from the encryption of profile database to that of locative media related information processing. The privacy concern of the latter has outgrown the former with latest shifts in the technology use and more pervasive forms of information sharing.
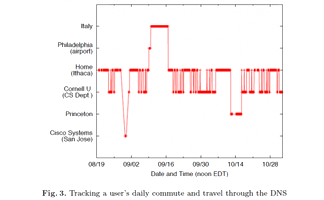
The Improvable Me
Who is the 'Improvable Me?'
The Improvable Me is the result of a built-up online reputation on top of a bad, or a damaged one.
"When you Google your name and found the first result being listed is something disgraceful. What you can do is you create a whole bunch of new information about yourself and make that the top results of Google search." - Hasan Elahi
Even you are very regretful about what you have said online. Don't delete them all.
It's even more problematic to have no background than an imperfect but believable background.
The Discovery of the 'Improvable Me'
In the collective practice of information sharing, our reputation is not purely controlled by oursevles, but also monitored and curated by everyone else. Even I do not post anything about myself, you can still find me, as I cannot guarantee that my friends will not mention my name or tag me in a picture. Tt difficult for single users to set out and moderate their reputation from time to time. However, exposing one to the various ways others use to access their information will assist the management for shared content and prevent some particular audience discovering the private content.
Thinking on the flip side: What cannot be searched also matters
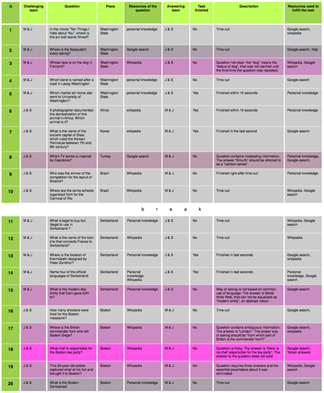
This is an observational research that aims to discover adaptive patterns of using search engines for competitive tasks. The rule of the game requires each team to raise and answer 10 questions to the opponents in the given time, using any online search engines. It was found that as the game continued, the players tended to hide the correct answers from the opponents by raising ambiguous and deceptive questions, a strategy quickly adopted by both teams under the awareness to the algorithmic pattern of the search engine.
The chart on the right listed all the questions being asked with the most misleading ones(as voted by the participants themselves) highlighted in red. The intensity of the color indicates the level of ‘trickiness’ for the questions. It demonstrated that with increased experience, the participants became more concerned about the keyword or resource the opponents can use to find the answer quickly, therefore avoiding using that keyword or changing it to a misleadingly term.
Video: The flow of the game
Video: The question "What is the modern day entity that 'Cern' gave birth to?"
The Invisible Me
1 / 2 / 3 / 4 / 5 / 6 / 7 / 8 /
Who is the 'Invisible Me?'
The 'Invisible Me' is an anonymous identity due to a missing link or a mismatch between the virtual identity and the real person.
The value of the 'Invisible Me' is rewarding especially when the identity used to be more public, exposed or discussed.
"The fact that gossip in cyberspace is recorded, permanently retrievable, and globally accessible increases the risk that an individual’s public face threatened by past indiscretions." - Jeffrey Rossen
The Discovery of the 'Invisible Me'
Too much data erases the identity?
The idea of the 'Invisible Me' came from the interview with Hasan Elahi, an interdisciplinary media artist known for his 7-year-long self-tracking project that helped him escape the terrorist watch list of U.S government. Though the original purpose of the project is to create an alibi that reports his activity through recording and updating it every ten minutes, Hasan has noted, however, his identity became more anonymous, to any ordinary audience, as the humongous amount of data accumulated over time has made interpretation to his identity impossible.

From famous to anonymous: the right strategy
A radical erasure can be an unnatural gesture, such as the over 244,000 houses on Google street view in Germeny. The result departed from the original purpose: instead of being invisible, the blurred houses stand out, seducing further curiosities to their presence.
What is the right strategy to escape from the public attention while continuing the conversation in a micro community?
The project 'Hack a structure' is a series of re-imagined public space addressing the question. As the digital and physical infrastructure become intertwined and both comment on our presence on social occasions, the visibility of our identity can also be adjustable.

Teach the Internet how to forget
The erasure of an identity is more complex than a temporal escape from the public. Especially because one cannot delete information from the memory of others, and to advocate something opposite to the propaganda is almost as useless as admitting it.
However one can become anonymous by controlling the access to their data, e.g, tracking down who has been 'cyber stalking' them. One can re-prioritize the information to be known by the public overtime, making the 'least secure' version of their identity 'most scarce' and 'hard to find'.
In reality, some data-brokers are already on the way to assist management of historic personal data.For example, Allow Ltd. helps one erasing personal information from as many marketing databases as possible, to ensure the scarcity of the data source provided by itself. It sounds like a massive cleaning job. However, facing up to the life expectancy of personal data and drawing a line to the ever-expansion of identity data trash is the first step to claim the ownership to our digital selves.
Research and References
The project is informed by an on-going discourse about social media users' virtual identity and its security resulted from the increasingly publicized personal data, and is greatly inspired by anecdotes and stories of using technologies to selectively hide from and lie to members in one's virtual network for varied social purposes, which also has an impact on one's real-world relationships.
Two questions have emerged and have driven the observational and analytical research that follows: (1)Can these behaviors inspire the design of social networks? (2)What should the design also afford as one’s virtual and physical identities collide or overlap with each other?
These researches have led to the summary of four main typographies of dishonest behaviors and their outcomes, namely the 'Augmentable Me', the 'Believable Me', 'Improvable Me' and the 'Invisible Me'. A design prototype for new experiences of social networking is created based on these identity models. Using the speculative research method, a narration is composed to contemplate the approaches and problems of the design by putting it into a series of imagined happenings.

References
[1]TechCrunch(2010). Check(In) Yo’Self Before You Wrech Yo’ Self: Why Foursquare Users Check In “Off the Grid”. http://techcrunch.com/2010/08/28/foursquare-off-the-grid/
[2]Erick Schonfeld(2009). We All Live In Public Now. Get Used to It. http://techcrunch.com/2009/12/30/we-all-live-in-public/
[3]Laurent Haug (2010). Following up on “Publicy”. http://liftlab.com/think/laurent/2010/01/02/following-up-on-publicy/
[4]Dan Ariely(2009). Why We Think It’s OK to Cheat and Steal(Sometimes). http://www.youtube.com/watch?v=nUdsTizSxSI
[5]Sarah Perez(2010). Facebook Declares “Zero Tolerance” for Data Brokers. http://www.readwriteweb.com/archives/facebook_declares_zero_tolerance_for_data_brokers.php
[6]Linguistic Inquiry and Word Count. http://www.liwc.net/, http://analyzewords.com/index.php
[7]Jacqui Cheng(2006). Technology use invites lying, says survey. http://arstechnica.com/science/news/2006/12/8513.ars
[8]Azeem Azhar(2011). Online Communities and Reputation Management. http://liftconference.com/lift11/program/talk/anonymous-online-communities-looking-beyond-obvious
[8]Dan Tynan(2011). How to Protect Your Privacy and Make Money Doing It. http://www.itworld.com/internet/138582/how-protect-your-privacy-and-make-money-doing-it
[9]Christian Rudder(2010). The Big Lies People Tell In Online Dating. http://blog.okcupid.com/index.php/the-biggest-lies-in-online-dating/
[10]Riley McDermid(2010). Worried About Your Reputation? Intelius Now Lets You Track It Online. http://venturebeat.com/2010/12/06/worried-about-your-reputation-intelius-truerep-now-lets-you-track-it-online/
[11]The Wall Street Journal(2010). What They Know. http://blogs.wsj.com/wtk/
[12]Dourish, P. and Anderson, K. 2006. Collective Information Practice: Exploring Privacy and Security as Social and Cultural Phenomena. Human-Computer Interaction, 21(3), 319-342.
[13]Daniel Nanavati(2010). A Brief History of Lies. CreateSpace.
[14]Dan Saffer(2007). How to Lie with Design Research. http://www.odannyboy.com/blog/new_archives/2008/01/how_to_lie_with_1.html
[15]Electronic Privacy Information Center. http://epic.org/
[16]Madrid Privacy Declaration(2009). http://thepublicvoice.org/madrid-declaration/
[17]Electronic Frontier Foundation(2008). Surveillance Self-Defense Project. https://ssd.eff.org/
[18]Oliver Burkeman(2011). SXSW 2011: The Internet is Over. http://www.guardian.co.uk/technology/2011/mar/15/sxsw-2011-internet-online
[20]M.D. Certeau(2002). The Practice of Everyday Life, University of California Press.
[21]Meredith(2010). Ypulse Interview: Dr. Genevieve Bell, Intel. http://www.ypulse.com/ypulse-interview-dr-genevieve-bell-intel
[22]Chris Matyszczyk(2010). Google Shows off Blurry New German Homes. http://news.cnet.com/8301-17852_3-20021429-71.html
Credits
Advised by: Sean Donahue, Molly Wright Steenson, Elise Co and Mike Milley.
Thanks to: Aarti Vashisht, Scott Liao, Norman Klein, Hasan Elahi, Noah Wardrip-Fruin Saikat Guha and Ian Sander for their precious opinions.
Thanks to: Dustin York for co-designing exhibition and sharing of knowledge.
Thanks to: Jayne Vidheecharoen, Salvador Orara, Michael Manalo, Ji Su Cho, Shannon Herbert, Tim Stutts, Ben Combee, Rubina Ramchandani and Ricky Wong for research participation.